Optical ByPass Switching
Optical Bypass Switches
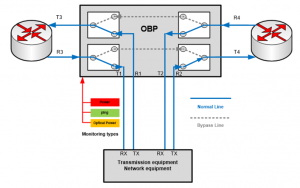
A bypass switch (or bypass TAP) is a hardware device that provides a fail-safe access port for an in-line active network device such as an intrusion prevention system (IPS), next-generation firewall, network switch etc. if the device loses power, experiences a software failure, or is taken off-line for updates or upgrades, traffic can no longer flow through the critical link. The bypass switch or bypass tap removes this point of failure by automatically ‘switching traffic via bypass mode’ to keep the critical network link up.
A bypass switch has four ports. Two network ports create an in-line connection in the network link that is to be monitored. This connection is fully passive; if the bypass switch itself loses power, traffic continues to flow unimpeded through the link.
Two monitor ports are used to connect the in-line device. During normal operation, the bypass switch passes all network traffic through the network (CPE) switch as if it were directly in-line itself. But when the switch (CPE) loses power, is disconnected, or otherwise fails, the bypass switch passes traffic directly between its network ports, bypassing the CPE, and ensuring that traffic continues to flow on the network link.
A bypass switch monitors the health of the CPE by sending heartbeats to the network switch (CPE) as long as the network device/switch is on-line, the heartbeat packets will be returned to the optical bypass switch and the link traffic will continue to flow through the CPE.
If the heartbeat packets are not returned to the Optical Bypass Switch (CPE has gone off-line), the Optical Bypass will automatically bypass the CPE and keep the link traffic flowing. The Optical Bypass also removes the heartbeat packets before sending the network traffic back onto the critical link.